一般来说c++ shared_ptr 实现逻辑上基本上都是一个ptr加上一个control block来实现,
control block 用于保存引用计数以及如何回收(deleter)等信息,
有一些实现(gcc)会将ptr放到control block里,
有的(llvm libc++)则分开存放, 两种实现没有本质上的区别.
braft call graph
This is the call graph of braft, an industrial grade raft implementation, which may help you understand braft better, I guess.
Clock And Timestamp
1 Preface
这篇文章总结了几个分布式数据库系统中常用的时钟算法, 主要包括: 中心授时服务, Google True Time, NTP, Logical clock, HLC.
花了比较大篇幅描述HLC的算法实现以及它的优缺点.
2 Why do we need clock/timestamp in (distributed) DBMS?
为什么需要时钟 -> 因为需要mvcc -> 为什么需要mvcc -> 因为事务需要锁, 需要解决事务冲突冲突
为什么不能使用本地时间? 如果使用本地时间, 没法保证内部系统的数据一致性(由于时间不统一, 节点1写入数据在 节点2可能读不到).
3 Terminology
memory ordering
1 Preface
Memory ordering describes the order of accesses to computer memory by a CPU. The term can refer either to the memory ordering generated by the compiler during compile time, or to the memory ordering generated by a CPU during runtime.
This post tries to explain memory ordering in a bottom-up approach, from hardware to software, from abstraction of memory order and memory model to language and application level.
This post covers the following questions
- How hardware/processors reorder out program (instructions)?
- What is memory model and memory order?
- How to understand it on a high level?
- How to use it (lock-free programming)?
list initialization and std::initializer_list
C++, C++11, initializer_list, emplace, emplace_back, list initialization
time: 2019-03-10-Sun 02:29:50
List initialization, since C++11
List initialization is a “new” syntax support (sugar) since C++11, the main
idea is to initialize object with a given list of arguments in enclosed brace
for initialization.
direct-list-initialization
T object { arg1, arg2, ... }; (1)
T { arg1, arg2, ... } (2)
new T { arg1, arg2, ... } (3)
Class { T member { arg1, arg2, ... }; }; (4)
Class::Class() : member{arg1, arg2, ...} {... (5)
gcc address sanitizer
c++, gcc, memory leak, sanitize, address sanitizer, leak sanitizer
time: 2018-12-13-Thu 21:38:55
AddressSanitizer (detects addressability issues, including leaks) and
LeakSanitizer (detects memory leaks)
Brief Thinking of RSA
public key and private key
- get 2 (big) primes,
pandq - find
nwhich is the key divider, wheren = p * q phi(n) = (p - 1) * (q - 1), in whichphi(n)is called Euler function- public key
e(short for its purpose encryption), which requires that:1 < e < phi(n)eandphi(n)are coprime (no common factor)
- private key
d(short for its purpose decryption), which requires that:(e * d) % phi(n) == 1
And all we need for encryption and decryption is n, e and d.
unicode
unicode, utf8, utf16, replacement char, UTF-8, UTF-16, UTF-32
created: 2017-10-30-Mon 14:05:42
update: 2019-10-17-Thu 22:03:57
Unicode, UCS-2, UCS-4,
UCS is short for universal character set, and unicode is an implementation for that.
UCS-2 simply uses two bytes (16 bits) for each character but can only encode the first 65,536 code points, the so-called Basic Multilingual Plane. With 1,114,112 code points on 17 planes being possible, and with over 120,000 code points defined so far, many Unicode characters are beyond the reach of UCS-2. Therefore, UCS-2 is obsolete, though still widely used in software. UTF-16 extends UCS-2, by using the same 16-bit encoding as UCS-2 for the Basic Multilingual Plane, and a 4-byte encoding for the other planes. As long as it contains no code points in the reserved range U+0D800-U+0DFFF, a UCS-2 text is a valid UTF-16 text.
Floating point, IEEE754
build with version injection
java, c++, go, version, build, maven, ant, g++
time: 2016-08-17-Wed 21:37:03
in many cases we need to update the version info in source file manually before release, however, we often forget to update them, because it’s a “concealed” bug before release
we can use some scripts to automate the procedure to inject version info into source file
java
terminal shortcut and function keys
xterm, terminal, shortcut keys, function keys
time: 2016-07-16-Sat 14:36:57
Xterm and other terminals through terminal control characters based on the type of terminal emulation. Commons terminal type are VT100…
Note: Most of these keystrokes come from the readline library, and have nothing to do with the terminal type or terminal emulator used (except that some terminals emulators don’t play well with control/meta keys). When using bash (which uses readline), a list of shortcuts it offers is obtained by entering “bind -P” at the command prompt.
json parser
This is a practice of parsing a json string with c++.
the sandard is from https://www.json.org
State machine
We usually use state machine to solve the string-paring problems.
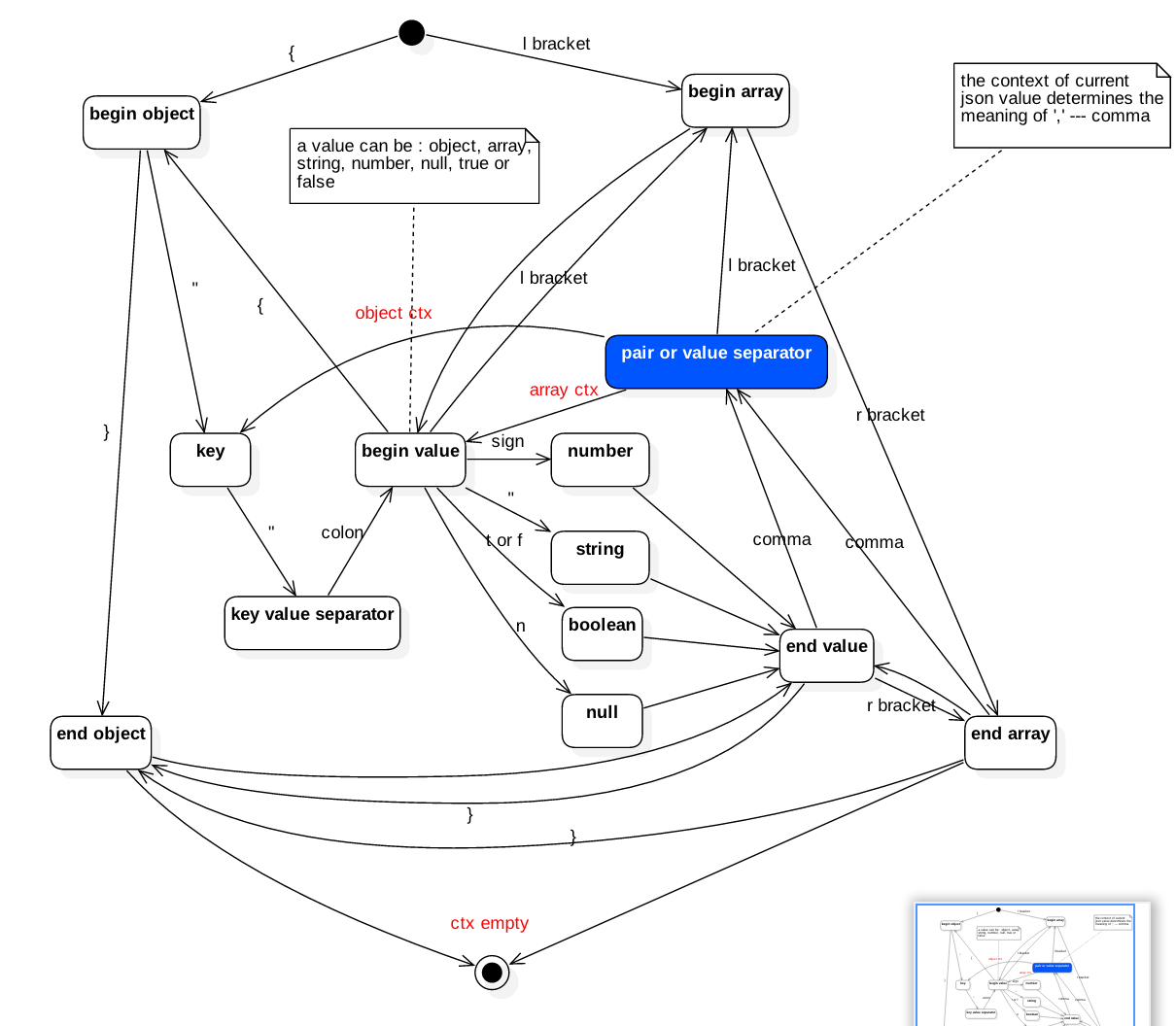
Implementation in c++
gflags' How-To and Tips
-
define flags in header files or cpp files which invoke the flags
define flags with initial values
DEFINE_bool(debug_mode, true, "if debug mode enabled"); DEFINE_int32(port, 8899, "TCP port for server"); DEFINE_int32(libbp_log_level, 4, "explanation");
std::pair syntax sugar
std::pair<T1, T2> syntax sugar
通常标准库的函数(multimap::equal_range, map::insert等)或者会返回一些std::pair,
这些pair中的first, second有的代表lowerbound, upperbloud, 有的代表是否插入成功以及
相应的插入位置, 在代码比较多的时候往往不是那么好记.
另外, 当我们自己想用pair来代表两个有一定关联的数据的时候, 最直接的方式是使用std::pair,
但是pair中的first, second又不是那么的能表达代码的含义.
